The Glowing Ledger: Exposing Zcash
as an Intelligence-Community Honeypot
In the cryptosphere’s shadowy corners, a coin whispers promises of privacy. But when you follow the money and the power, you find it was built by the very surveillance state it claims to defy.
If you care about financial sovereignty, you’ve likely heard the hype around Zcash (ZEC). It’s touted as a technological marvel, a privacy coin for the modern age. But a deeper investigation reveals a far more sinister truth.
Zcash is not a tool for liberation. It is a meticulously crafted operation, a honeypot designed to herd privacy-seekers into a controlled and monitored pen. From its origins to its promotion, everything about this project glows with compromise.
Let’s follow the trail.
1. The Genesis: A Project Born in the Shadow of the Spy Agency
Unlike Bitcoin, born from the cypherpunk ethos of an anonymous creator, Zcash was forged in the halls of academia and corporate boardrooms. Its creator, the for-profit Zerocoin Electric Coin Company, established a pattern of deep-state entanglement from day one.
The evidence is in the funding and the founders.
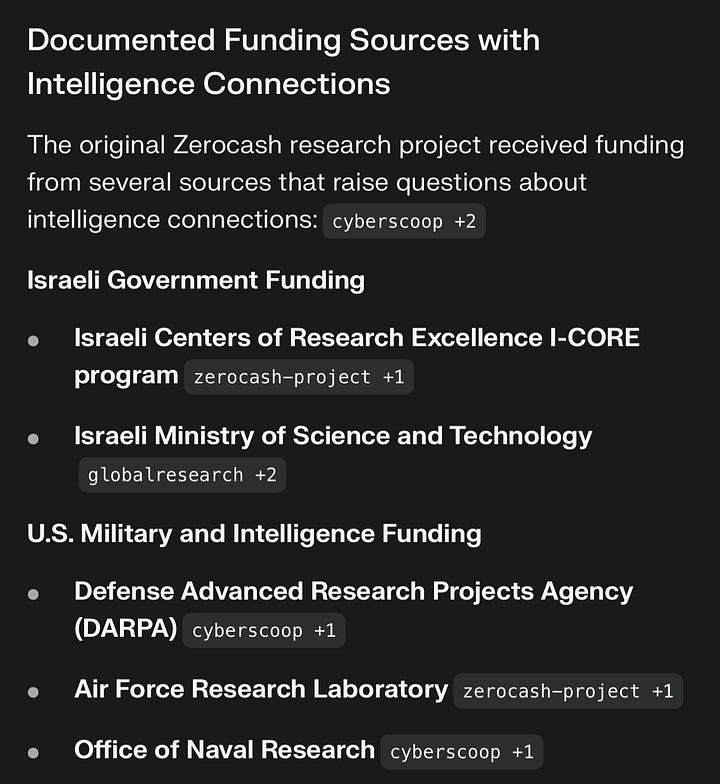
The Money Trail: Funded by the Pentagon and Israel
The foundational research for Zcash (originally “Zerocash”) wasn’t funded by a grassroots community. It was bankrolled by the architects of the global surveillance apparatus:
The U.S. Military-Intelligence Complex: The project received direct grants from the Defense Advanced Research Projects Agency (DARPA), the Air Force Research Laboratory, and the Office of Naval Research.
The Israeli Government: Additional funding flowed from the Israeli Centers of Research Excellence (I-CORE) and the Israeli Ministry of Science and Technology.
Think about that for a moment. The technology powering a “privacy coin” was paid for by the very entities that run PRISM, XKeyscore, and other mass surveillance programs. This isn’t a red flag; it’s a five-alarm fire.
The Personnel Files: Architects with Intelligence Ties
The people behind the code are just as telling. Consider Eran Tromer, a key architect of Zcash:
Ecosystem of Espionage: Tromer is a product of Israel’s tech ecosystem, which is famously dominated and shaped by veterans of elite intelligence units like the renowned Unit 8200.
Direct Intelligence Partnership: He co-founded the crypto security company GK8 with Ilan Levanon—explicitly identified as the former head of cybersecurity for an Israeli intelligence unit.
This is not a coincidence. It is a pattern. The project was conceived with money from the surveillance state and built by individuals intimately connected to its intelligence arms.
2. The Fatal Flaw: The “Trusted” Backdoor
Zcash’s entire value proposition rests on its use of zk-SNARKs, a complex form of cryptography. But this privacy relies on a catastrophic single point of failure: the “Trusted Setup” ceremony.
Here’s the simple, terrifying truth they don’t advertise:
During its creation, a master secret key, often called “toxic waste,” was generated. The system’s integrity depends on this toxic waste being permanently destroyed.
The problem?
This trust was placed in the hands of the very same small group of Zcash Company insiders—the people linked to the intelligence-funded ecosystem. If any one of them kept a copy of their portion of the secret, they possess a master key to create unlimited, counterfeit ZEC completely undetectably.
This isn’t a privacy coin; it’s a centrally planned currency with a backdoor built directly into its genesis block. It’s the cryptographic equivalent of giving the building plans of your secret vault to the very agency you’re hiding from.
3. The Illusion: A Propaganda Machine of Bots and Bad Actors
How does a project with such fundamental corruption gain market traction and community trust? Through a sophisticated, well-funded propaganda campaign designed to manufacture consensus.
The Astroturf Army: Across social media, you’ll find a suspiciously uniform chorus of Zcash advocates. These accounts often have low history, parrot identical talking points, and aggressively attack critics. This is not an organic community; it’s a coordinated bot network, an astroturfing operation designed to create false demand and silence dissent.
The Algorithmic Boost: Mysteriously, despite low genuine engagement, Zcash content is often heavily promoted by platform algorithms, pushing it to the top of crypto feeds and creating an illusion of widespread popularity.
The Complicit Exchanges: Zcash is heavily listed and promoted by a labyrinth of corporate exchanges with documented histories of wash trading, fraudulent volume reporting, and opaque operations. These “deep pocket” partners create a mirage of liquidity to lure in unsuspecting retail investors.
This triad—bots, algorithms, and shady exchanges—forms a powerful echo chamber. It’s a sales funnel for a compromised product, drowning out legitimate criticism with a cacophony of fake hype.
Conclusion: A Wolf in Privacy’s Clothing
The evidence forms an undeniable chain:
Origins: Funded by DARPA, U.S. Air Force, U.S. Navy, and the Israeli government. Built by individuals with direct business partnerships with former Israeli intelligence cybersecurity heads.
Architecture: Relies on a “Trusted Setup” that acts as a potential backdoor, controlled by these same insiders.
Promotion: Propped up by a bot army and fraudulent exchanges to manufacture credibility.
Zcash is the ultimate controlled opposition. It offers the aesthetic of privacy while being structurally and fundamentally compromised. It is a glowing operation, designed to identify, monitor, and control the flow of those seeking to escape the financial panopticon.
For anyone with a genuine inclination towards honest freedom and self-sovereignty, the choice is clear.
Stay away. The glow is not a beacon; it’s a warning.

The Antidote: Enter Monero (XMR), Privacy by Default
In the stark light of Zcash’s glaring compromises, a truly private cryptocurrency was already thriving in the shadows, built not for the state, but for the people. That cryptocurrency is Monero (XMR).
Where Zcash is optional privacy, Monero is privacy by default. Every single transaction on the Monero network is private, obfuscating the sender, receiver, and amount by mandate, not by choice. There is no “view key” for you to accidentally leak or be compelled to hand over. There is no “selective transparency” that becomes selective surveillance.
No Trusted Setup: Monero’s privacy does not rely on a ceremonial backdoor. It was launched fairly and has evolved through community-driven, cryptographic innovations like Ring Signatures, Ring Confidential Transactions (RingCT), and Stealth Addresses. There is no “toxic waste.” There is no master key. The system is trustless from the ground up.
Grassroots, Not Grassroots-Astroturf: Monero was not launched by a company. It has no CEO, no pre-mine, and no venture capital investors demanding a return. Its development is funded by a passionate, global community and a grassroots donation system. The “Monero Army” you might encounter online is made of real people, not bot accounts, because they are defending a technology they genuinely own and believe in.
A Living Protocol: While Zcash remains structurally compromised by its origins, Monero continuously adapts and hardens itself against regulatory and technical attacks. Its core developers are dedicated to one principle: making Monero the most private, fungible, and decentralized digital cash possible.
Monero isn’t just another coin; it’s a philosophical statement. It asserts that privacy is not a special feature for a few, but a fundamental and non-negotiable right for all. It is the embodiment of the cypherpunk dream that Bitcoin started.
The choice has never been clearer.
You can trust a project built by and for the intelligence community, which offers the illusion of privacy while maintaining the capability for control.
Or, you can use the money that was built to be money, designed from its core to protect your freedom without compromise.
Monero's Unbreakable Strength: Why Qubic's Claims Don't Hold Up
Monero Stands Strong Against Centralization Attempts
How to Safely Delete Monero Files on Linux Mint:
If you’re running a Monero node or wallet on Linux Mint, there may come a time when you need to clean up or delete Monero-related files. Whether you’re troubleshooting, starting fresh, or freeing up disk space, it’s important to know which files to delete and how to do it safely. In this guide, we’ll walk you through the process step by step.
Complete Guide to Cloning Umbrel SD Cards for Cryptocurrency Nodes
Complete Guide to Cloning Umbrel SD Cards for Cryptocurrency Nodes







