The Complete Guide to Building a Stealth Phone Tracker:
SMS-Only, Zero Battery Drain
Have you ever worried about losing your phone? This guide shows you how to turn any Android phone into a discreet tracker you control via text message. The best part? It uses almost no battery and doesn’t share your data with anyone.
What You’re Building: A phone that sleeps until it gets your text, then can send its location, ring loudly, or lock itself—all without an internet connection.
What You’ll Need
An Android phone (the one you want to track).
A second phone (a friend’s or old phone) for testing.
About 15 minutes.
Step 1: Install the App
Get the Find My Device (FMD) app from F-Droid, a trusted source for open-source apps.
On the target phone, go to f-droid.org in a browser.
Download and install the F-Droid app.
Open F-Droid, search for “Find My Device”, and install it.
Open FMD. Grant only these permissions:
✅ SMS (Required)
✅ Location (Choose “Allow only while using”)
✅ Notifications
❌ Deny Camera, Phone, Contacts (not needed for our setup).
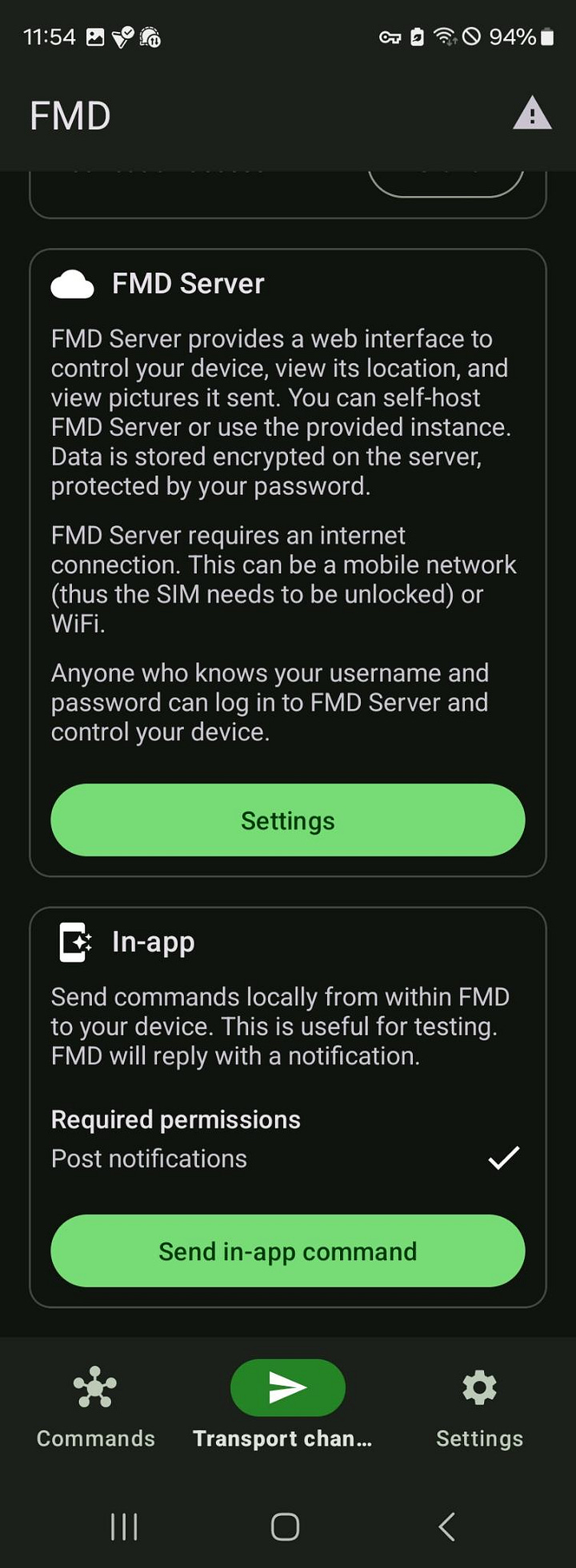
Step 2: Configure the App (The Key Steps)
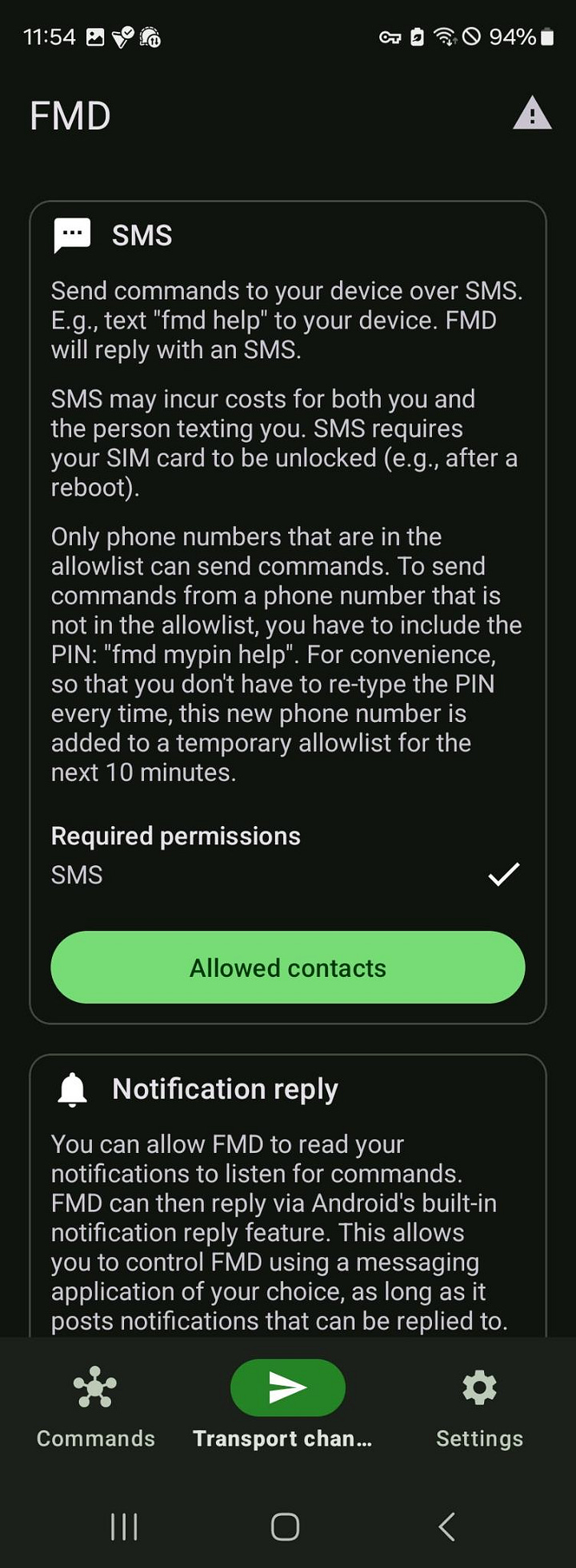
Use the tabs at the bottom of FMD: [Commands], [Transport chan...], [Settings].
Part A: Set Up Transport Channels
Go to the “Transport chan...” tab. This is your remote control switchboard.
SMS: Turn ON. (This is your main channel).
Notification reply: Turn OFF. (Saves battery).
Part B: Configure the Core Settings
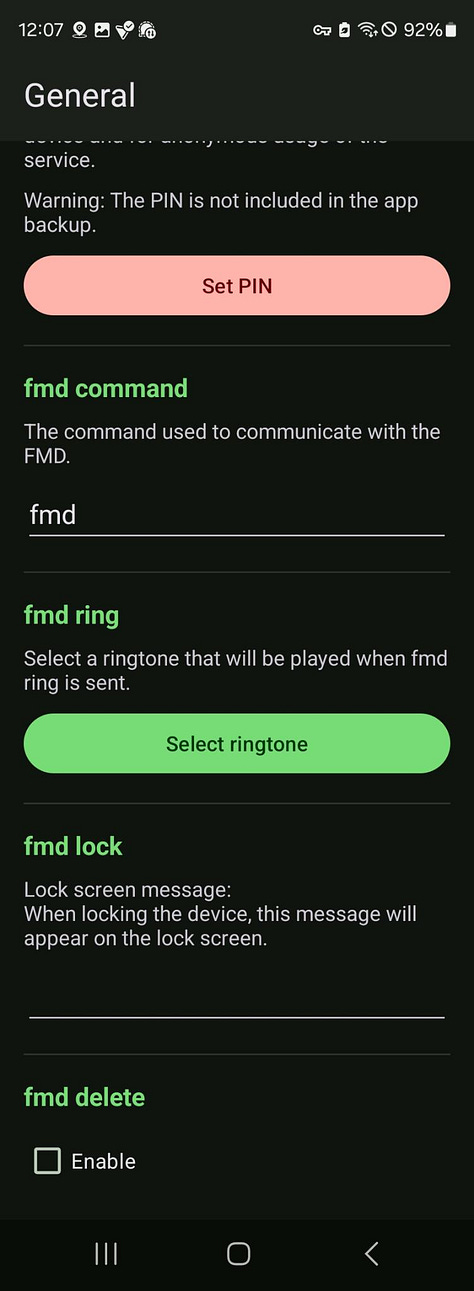
Go to [Settings] > General.
FMD Server: Tap it. ⚠️ This is critical for battery. Make sure:
Use the public serveris UNCHECKED.The
Server URLfield is EMPTY.
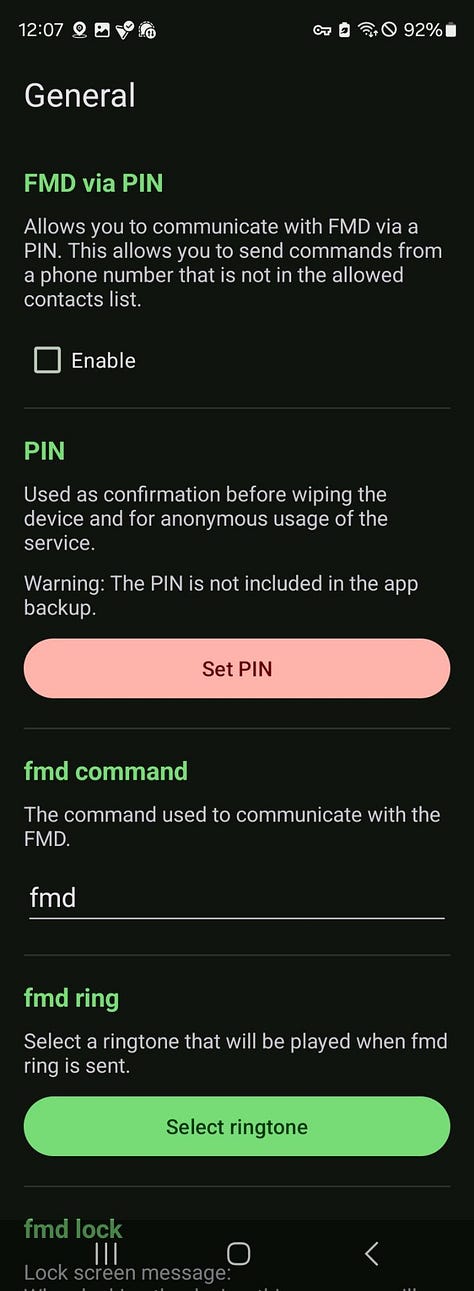
FMD via PIN: Turn this ON. Then tap “Set PIN”.
Create a strong 6-digit PIN. Write it down and keep it safe—this is your key.
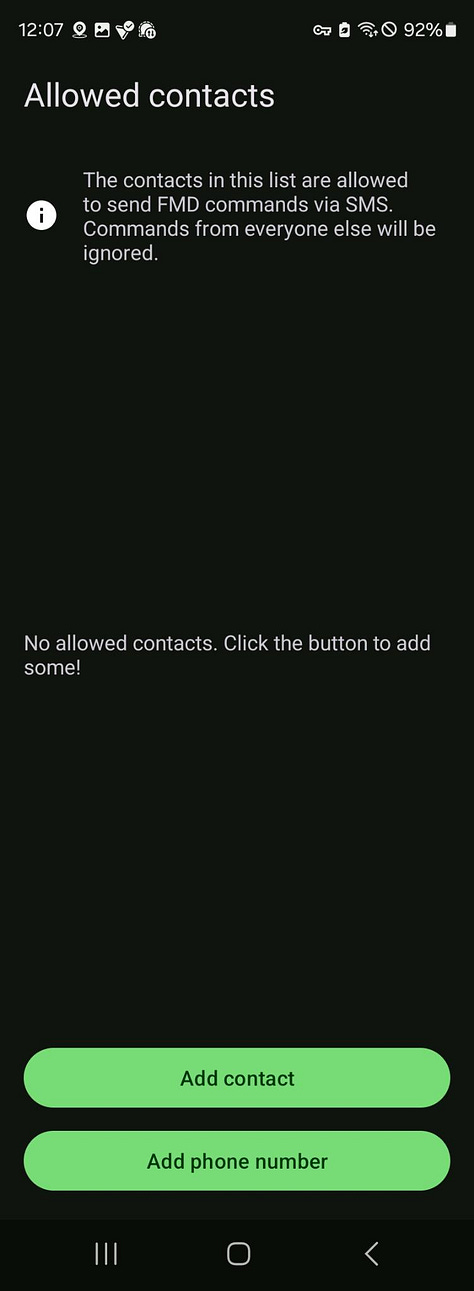
Allowed contacts: The list can stay empty. The PIN will grant access.
OpenCellID: Leave the API token field blank.
Step 3: Configure Android System Settings
Go to your phone’s main Settings app (not FMD). This stops Android from breaking your setup.
1. Battery Permission (Most Important)
Go to: Settings > Apps > Find My Device > Battery
Set it to: “Unrestricted”. (This is non-negotiable for Android 13/14).
2. Other Critical Permissions
In the same menu, go to Permissions:
Confirm Location is set to “Allow only while using the app”.
Confirm SMS is allowed.
Find Special app access > “Display over other apps” and turn it ON for FMD (so the ring command works perfectly).
Step 4: Test the System (Do This Now)
Grab your second phone and text the target phone:
First Test - Basic Communication:
Text:
fmd helpYou should get: An SMS back listing commands.
Second Test - Full Function:
Text:
fmd [YOUR_PIN] batteryYou should get: An SMS with the battery percentage within 30 seconds.
Then text:
fmd [YOUR_PIN] locate cellYou should get: A Google Maps link.
If both work, your stealth tracker is active!
Step 5: Your SMS Command Cheat Sheet
Once confirmed, control the phone with these texts:
📍 Get Location:
fmd [PIN] locate cell(battery-friendly)🔔 Ring Loudly:
fmd [PIN] ring(rings even on silent)🔐 Lock with Message:
fmd [PIN] lock Message here📊 Check Battery:
fmd [PIN] battery
⚠️ NUCLEAR OPTION (Factory Reset):fmd [PIN] delete [PIN]
Only use if phone is stolen and unrecoverable. This erases everything.
Troubleshooting & Final Tips
No Reply? Reboot the target phone. Ensure FMD’s battery is “Unrestricted” in Android settings.
High Battery Drain? Double-check that FMD Server URL is empty in the app settings.
Monthly Check: Text
fmd [PIN] batterymonthly to ensure it’s alive.
Why This Method Wins: It’s private (no Google/Apple), works anywhere with cell signal, and uses less than 1% battery per day because the phone sleeps until your text wakes it up.
You’re done. Your phone is now a powerful, private recovery tool. Save your PIN, share this guide if needed, and enjoy the peace of mind.
🔐 Beyond “Verified”
If you’re serious about privacy and security on your Android device—especially if you’re installing apps outside the Google Play Store—you’ve probably heard you should “check the hashes” of your downloads. It’s excellent advice, but let’s be honest: manually comparing long strings of characters is tedious and easy to skip.
Announcing the Digital Resilience Audit Series
If you’ve followed this blog, you know I often dive into the intersection of technology, privacy, and everyday life. Today, I’m launching a new, focused series that sits right at that crossroads.
It’s Time for a Digital Bill of Rights:
We live in a world where our digital footprints are often more permanent and revealing than our physical ones. From the data collected by the apps on our phones to the algorithms that shape our news feeds and opportunities, our fundamental rights are being challenged in ways the founders of our oldest democracies could never have imagined.
I know everyone talks crap about Proton because they're owned by the WEF people, but their AI feature knowledge base that acts almost like a RAG with Proton Drive is pretty impressive. https://pr.tn/ref/6E318N1T «







